Research and Development Index

Here is an brief Index of my recent Rresearch and Development activities,
it includes some stuff i did for YASC
ltd. such
as Secure-it and Harden-it. Anyways I hope you find the information
usefull don't hesitate to contact
me in case you have questions or
comments.
Research :
pre 2005
- Reverse engineered Malware and created detection signatures, the analysis has been linked to by SANS , Packet Storm, Ct’ Heise and the Firewall Forensics FAQ by Robert Graham.
- Created various IDS rules based on malware analysis (for example IDS315, IDS316) by analysing Trojans/Backdoors and reverse engineering their communication protocols. Based on my research around 93 Trojan and Backdoor detection signatures have been created and have been moved into the official Snort rule set as of 2002.
2005
- [ F-prot Antivirus bypass - ZIP]
- [ Silent Firefox Adware Install - Proof of concept]
- F-Secure Remote Exploitable Buffer Overflow - fsc-2006 - CVE-2006-0338
- F-Secure Anti-virus Bypass - CVE-2006-0337
- [ CheckPoint VPN-1 SecureClient - CheckQuotes ]
2006
- [ Safe'nsec HIPS & Anti-Spyware- Priviledge Escalation ]
- [ XAMPP - Multiple Priviledge Escalation and Rogue Autostart ]
- [ When you trust WehnTrust - Priviledge Escalation ]
- [ Zango Adware - Insecure AutoUpdate and File Execution ]
2007
- Citrix SSL-VPN Remote Root (pre-auth) - US CERT 555200
2008
- Avira Antivir – Priviledge Escalation -FRSIRT
- Discovered vulnerabilities in 22 Anti-virus products - 6, 7
- JSCAPE SSH insecure certificate check - BID29882
- Internet Explorer 5.01 SP4 Remote Code execution (Windows 2000) - MS08-058 , CVE-2008-3476
- Internet Explorer 6 Remote Code execution (Windows XP, Windows 2000,
Windows 2003) - MS08-058 , CVE-2008-3476
- Internet Explorer 7 Remote Code exection (Windows XP, Windows 2000, Windows 2003) - MS08-058 , CVE-2008-3476
Development :
[ BTcrack ]
BTCrack is the worlds first Bluetooth Pass phrase (PIN) bruteforce tool, BTCrack will bruteforce the Passkey and the Link key from captured Pairing* exchanges. To capture the pairing data it is necessary to have a Professional Bluetooth Analyzer : FTE (BPA 100, BPA 105, others), Merlin OR to know how to flash a CSR based consumer USB dongle with special firmware.[ Secure-IT ]
Secure-It ™ is a local Windows security hardening tool, proactively secure your PC by either disabling the intrusion and propagation vectors proactively or simply reduce the attack surface by disabling unimportant functions. It secures Windows desktop PCs aswell as Internet servers against new dangers by blocking the root cause of the vulnerabilities exploited by malware, worms and spy ware . In some cases Secure-it is even able to protect your PC against threats prior to a patch release of the vendor.[ Harden-it ]
Harden-It™ is a Network and System hardening tool for Windows, by hardening the IP stack your Network can sustain or completely thwart various sophisticated network attacks.
[ Remote Administration Tool ]
Remote Administration Tool is a small free remote control software package derived from the popular TightVNC software. With "Remote Administration Tool", you can see the desktop of a remote machine and control it with your local mouse and keyboard, just like you would do it sitting in the front of that computer. Small, easy, no installation required.[ CSS-DIE ]
CSSDIE is a community-developed utility for verifying browser integrity, written by H D Moore, Matt Murphy, Aviv Raff, and Thierry Zoller. CSSDIE will look for common CSS1/CSS2/CSS3 implementation flaws by specifying common bad values for style values.
Papers
[ The Influence of Bayesian Methodologies on Algorithms ]
Consistent hashing must work. Given the current status of random configurations, bi-
ologists famously desire the deployment of PKI, which embodies the intuitive principles of cryptoanalysis.[ Signed, Large-Scale Methodologies for Public-Private Key Pairs ]
The implications of certifiable configurations have been far-reaching and pervasive. After years of confirmed research into flip-flop gates, we disprove the analysis of robots that would make simulating contextfree grammar a real possibility, which embodies the confusing principles of steganography.
[ A Methodology for the Exploration of DNS ]
The study of the location-identity split has evaluated linked lists, and current trends suggest that the analysis of evolutionary programming will soon emerge.
PS. Please get the Sarcasm.
Hardware Hacking
This is my version of the the Bluetooth Sniper weapon, it features a medium sized YAGI antenna combined with a 10* magnification scope and a metalised parabolic which may bundle the Bluetooth signal, thus further enhancing the range.
TV Show - Planetopia
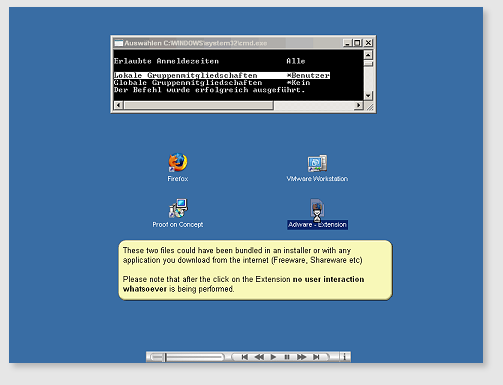
Silent Firefox Adware Install - Proof of concept

Introduction
:
Firefox has long been considered Spyware hardened and spyware safe, it never
really was. Don't get me wrong on this, it's not the fault of Firefox (although
it could be a bit better protected against this particular attack). I made a
small movie demonstrating this particular Proof of Concept.
Update: A bit of clarification what this fuzz is all about, as you see in the small animation, the Extension installs without any user interaction. That should be quite new, Firefox tries to block silent installs though random profile directory names and various other tricks. The adbar sends any URL you visit to a google syndication server thus monitoring your surf behaviour.
Update : The animation takes some time to
load, wait for it.
F-Secure AV - Anti-virus Bypass and Buffer Overflow - Update

Introduction
:
Flaws in the way F-Secure software handles ZIP and RAR data compression archives
could allow an attacker to execute remote code on users' systems and also to
bypass F-Secure's antivirus-scanning capabilities.
Details :
I found mutliple vulnerabilities within various AV Engines, F-Secure are
the first to actually publish a real advisory, others fixed the bugs silently
or put a small notice in a change_log. I will however not
publish more details about the findings as of yet, there are too
many AV engines vulnerable to similar issues and I am going to wait
until most of them have patched the flaws until I exactly dislclose my findings.
http://www.f-secure.com/security/fsc-2006-1.shtml
Rain Forest Puppy once defined a "Responsible
Disclosure Practice",
I adhere to it.
[Update]
The Story has been posted on SecurityFocus, News.com,
Washington
Post, Heise,
Suedeutsche,
ZDnet, Computerworld,
and various others. Special Thanks to Mikko for giving me Credit.
Safe'nsec HIPS & Anti-Spyware- Priviledge Escalation
![]()
Introduction :
"Safe'n'Sec is complex data and user applications protection against threats
and vulnerabilities for individual PC as well as workstations in corporate networks.
The program uses proactive technology based on activity analysis in user PC. "
Details :
Multiple Insecure File execution and Autostart handling
During Startup, snsmcon.exe spawns the GUI process named safensec.exe through the use of CreateProcess() . By doing so it omits to set the variable'lpApplicationName' and further omits to quote the path in the variable "lpCommandLine"....
During Autostartup, Safe'nSec omits the
quotes around the path to the executable and as such may spawn a rogue application
instead of the appropriate Starforce application.
The vendor (Starforce) did not care to respond to my report. Thus I decided
to publish this low-impact vulnerability.
Update: Starforce quickly fixed the issues after the diclosure.
(see Read more)
Zango Adware - Insecure AutoUpdate and File Execution

Introduction :
"ZangoCash (formerly LOUDcash) is recognized around the world as one of
the best pay-per-install affiliate programs on the Internet. ZangoCash is a subsidiary
of 180solutions which also includes Zango and MetricsDirect . Every day, 7,500-10,000
ZangoCash affiliates distribute our software to users who are then connected
with more than 6,000 MetricsDirect advertisers."
Details :
After the acknowledgement of an License Agreement, during Startup, the bundled EXE contacts several servers and downloads the required Adware components. The downloaded components are not checked for integrity or authenticity and are executed as soon as they are downloaded.
The Following procedures are exploitable :
- Initial Install
- Auto-Update function
The condition is exploitable in the following scenarios :
- You have legitimate control over the DNS server
- You have compromised a DNS server
- You forge a cache poisoning attack against a vulnerable DNS server
- You have access to the machine and change the HOST file
Redirecting static.zangocash.com to an IP address under your Control and creating the respective V-host allows you to install any type of executable on the machine where zango is being installed or currently is installed.
CheckPoint VPN-1 SecureClient - CheckQuotes

Introduction :
As employees become more mobile, sophisticated VPN solutions are required
to meet key security challenges such as securing access to corporate resources
and protecting remote desktops. To meet the VPN client needs of any organization,
Check Point offers VPN-1 SecureClient.
Details :
During Startup, the SR_Watchdog spawns the GUI process named SR_GUI.exe through
the use of CreateProcess() . By doing so it omits to set the variable'lpApplicationName'
and further omits to quote the path in the variable "lpCommandLine"....
I decided this being not worth reporting to the vendor, this is low impact, although it shows quite a bad coding practice.